At 10-Year Milestone, Microsoft's Trustworthy Computing Initiative More Important than Ever - Stories

Benefits of Using Trusted Computing Technology | Trusted Computing Platforms, the Next Security Solution | InformIT
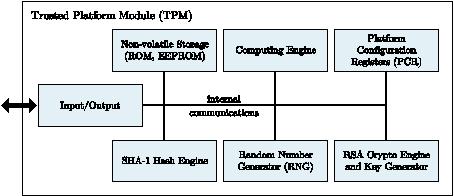
D3.9: Study on the Impact of Trusted Computing on Identity and Identity Management: Future of IDentity in the Information Society
All new Windows 10 PCs to have Trusted Platform Module 2.0 enabled by default with Redstone - MSPoweruser

Trusted Computing Group Releases TPM 2.0 Specification for Improved Platform and Device Security | Business Wire

European Centre for IT-Security ( eurobits ) 1 European Multilateral Secure Computing Base Open Trusted Computing for You and | Semantic Scholar
COTS-Based Trusted Computing: Getting Started in Next-Generation Mission-Critical Electronics | Curtiss-Wright Defense Solutions

The Core Concept of Access Control by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu